|
|
2 jaren geleden | |
|---|---|---|
| .. | ||
| images | 3 jaren geleden | |
| README.md | 2 jaren geleden | |
| README_RU.md | 2 jaren geleden | |
| cloud-init_lin.tpl.yaml | 3 jaren geleden | |
| main.tf | 3 jaren geleden | |
| provider.tf | 3 jaren geleden | |
| script.sh | 3 jaren geleden | |
| variables.tf | 3 jaren geleden | |
README.md
VM disk encryption in the cloud using YC KMS
Description
- The solution allows you to encrypt the disk (except the boot disk) on a Yandex Compute Cloud VM using Yandex Key Management Service and dm-crypt+LUKS.
- Deployment of the solution and prerequisites is performed using an example Terraform script.
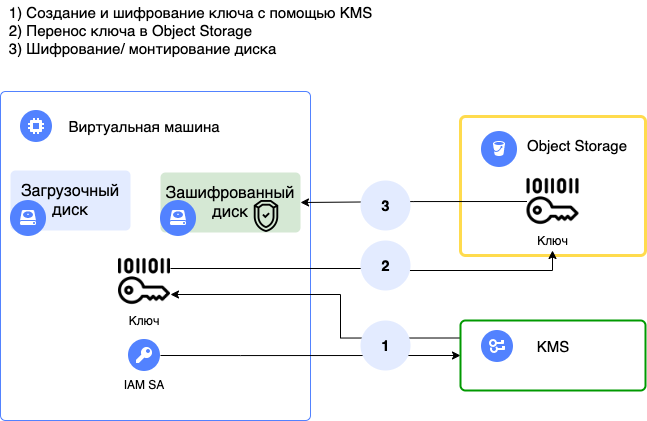
Operating diagram
Description of the solution operation
- Pass data to the cloud-init script when deploying a VM instance.
- Install the software: AWS CLI, cryptsetup-bin, curl.
- The SSH key created by Terraform is transmitted.
- A Bash script with the create argument is executed on the VM: a high entropy encryption key is created using the KMS generateDataKey method and then written to a disk in both a free-text and encrypted format.
- The second VM disk is encrypted and mounted based on the encryption key.
- The encrypted key is copied to Yandex Object Storage and deleted from the file system.
- A script with the "open" argument is added to the OS startup options to automatically mount the encrypted disk at reboot.
- At the time of mounting, the encryption key is downloaded from S3, decrypted, and then deleted from the file system when mounting is complete.
All operations with KMS and Object Storage are performed using a service account token linked to the VM at its creation.
Description of script arguments:
- create: Creating a high entropy key using the KMS generateDataKey method.
- open: Mounting an encrypted disk to a decrypted object.
- close: Unmounting an encrypted device.
- erase: Deleting the source device.
Prerequisites (configured using the Terraform script example):
- Install and configure YC CLI.
- Create a service account.
- Create a KMS key.
- Assign rights for the KMS key to the created service account (kms.keys.encrypterDecrypter).
- Create an Object Storage Bucket.
- Assign rights to the Object Storage Bucket to the created service account (storage.uploader, storage.viewer + BucketPolicy).
- Assign a service account to the VM.
- Install AWS CLI:
apt install awscli - Install cryptsetup:
apt install cryptsetup-bin
Launching the solution
- Download the files.
- Fill out the variables.tf file.
- Execute Terraform commands:
terraform init
terraform apply
Deployment results
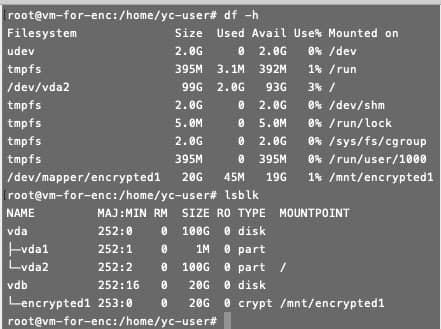
- Check the status of mounted objects:
lsblk
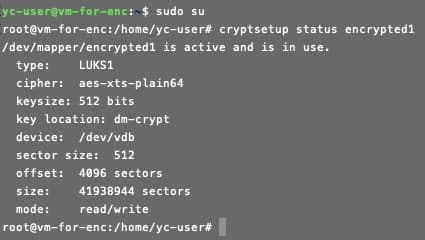
- Check the disk encryption status:
cryptsetup status encrypted1
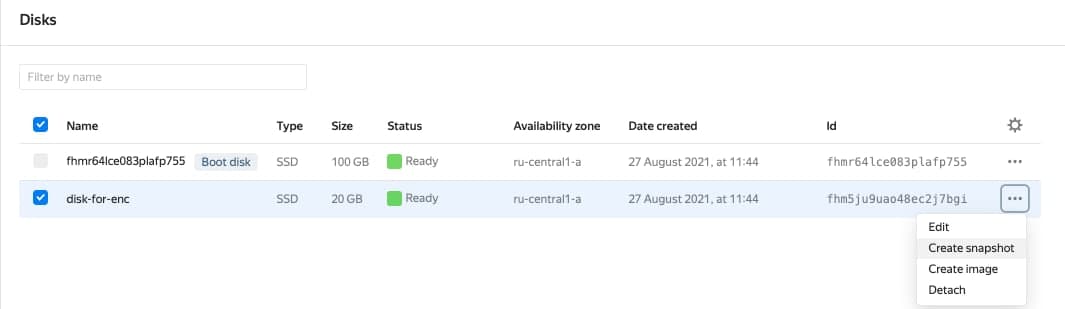
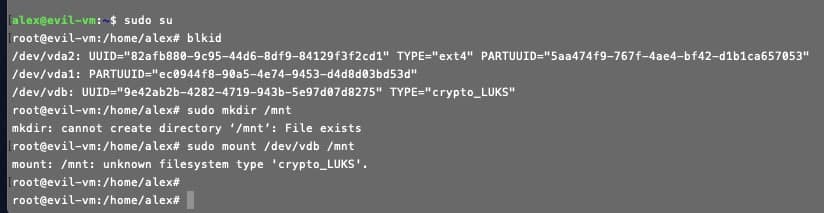
- Check the disk on another VM. To do this, create a snapshot of the disk:
sudo mount /dev/vdb /mnt